What is VMware Workspace One?
- Marcus Yeo
- Nov 4, 2018
- 2 min read
Updated: Jan 20, 2019
VMware acquired AirWatch in 2014, and integrated AirWatch to form part of the service offering in the Workspace One services, intended to directly address challenges faced by organizations in the consumerization of IT.
Workspace ONE is the simple and secure enterprise platform that delivers and manages any app on any device by integrating identity, application, and enterprise mobility management.
This blog covers my understanding of the VMware's Workspace One offering on the high level, and not intended to cover in depth on each of the services within Workspace One.
VMware Digital Workspace Portfolio consist of 3 pillars:
Desktop - Horizon 7, Horizon Air, Horizon Flex, UEM
Mobile - AirWatch
Application - AirWatch collaboration Apps, Horizon App Volume and ThinApp
VMware Identity Manager link these 3 portfolio together by providing a Single-Sign-On solution

Customer's Common Use cases
Balance end user's accessibility, ease of use and productivity VS security of organisation
Manage multiple devices of different platform
Secure device and data if device is lost or stolen
3 Workspace One Editions
Below is a simple illustrate the difference between the 3 editions. For more details, refer to VMware KB (https://www.vmware.com/content/dam/digitalmarketing/vmware/en/pdf/products/workspace-one/workspace-one-editions-comparison.pdf).

One Platform - All Employees, All Use Case
Workspace One allows IT to exercise policy enforcement while allowing employees convenience and privacy base on their preferences. AirWatch supports device management spanning across iOS, Android, MacOS, Windows 10, and Chrome OS.
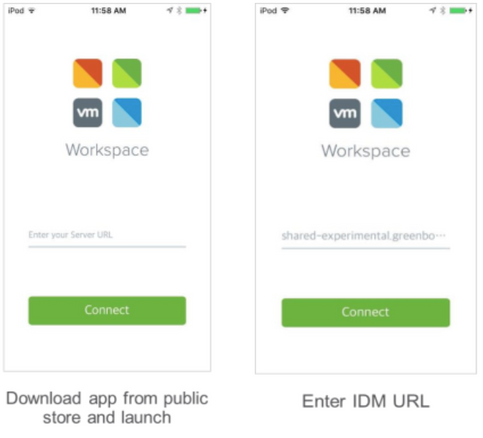
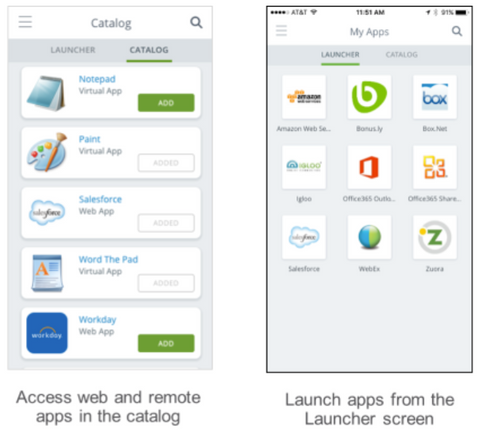
Employees only need to enrol their devices once by download and launch the Workspace One app from the public app store. Once authenticated to the app, employees can access and add cooperate application from 'Catalog' to the Launcher screen.
Managing both Managed and BYOD
This part is probably alittle bit more specific, but below is an interesting slide I came across explaining the workflow of VMware AirWatch and identity manager in the authentication of both cooperate and BYOD.
Users are first authenticate by SSO (Domain password)
-> Certificate/Device-Based Authentication (Unique device)
--> Multiple Factor Authentication (Eq. 2FA)
---> Conditional Access (Eg. by application)
----> Conditional Access ( Management for device posture/compliance)
-----> Automated protection based on real-time non-compliance

"What do you think?"
Let me know if you think there is any important/useful details I have missed in the above write up.





Comments